Synchronization has opened doors for unauthorized device linkage, access, and use. Indeed, a survey found that unauthorized smart device usage was a problem experienced by 43% of participants.
So, if the question “How to check if my phone is linked to another device” has been on your mind, now’s an excellent time to learn how.
After all, you don’t want to be a victim of such unlawful access, as it can compromise safety, privacy, and even your finances. It can also result in identity theft and fraud. Such crimes are rampant in the U.S.; in 2022 alone, the Federal Trade Commission received over 5.4 million reports.
That’s a good enough reason to keep your mobile devices secure and private. We’ll teach you how to verify if your phone links to other devices, so please read on.
How to Check if My Phone Is Linked to Another Device

If you use Gmail, it’s the first thing you should check for possible device linkages. Whether you’re using an Android or Apple, you’ve likely synced your Gmail or Google account to it.
Here are the steps to check if your Google Account and Android or Apple device links to other devices you don’t own or recognize.
Access Google Account Settings
You can access your Google account settings through your device’s Gmail or Chrome app. When you open either, you should see a small icon with your picture (if you have one) in the upper right-hand corner.
On the Gmail app, tapping that icon should bring up a window where you can select Manage your Google Account. On Chrome, it should bring up the Settings menu where you can tap your name (you may have to do it twice). You should then see and select the Manage your Google Account option.
On the Google Account settings menu, navigate to the Security tab. Scroll down to Your Devices. This should show all devices your Google account links to, such as your phone, tablet, laptop, or PC.
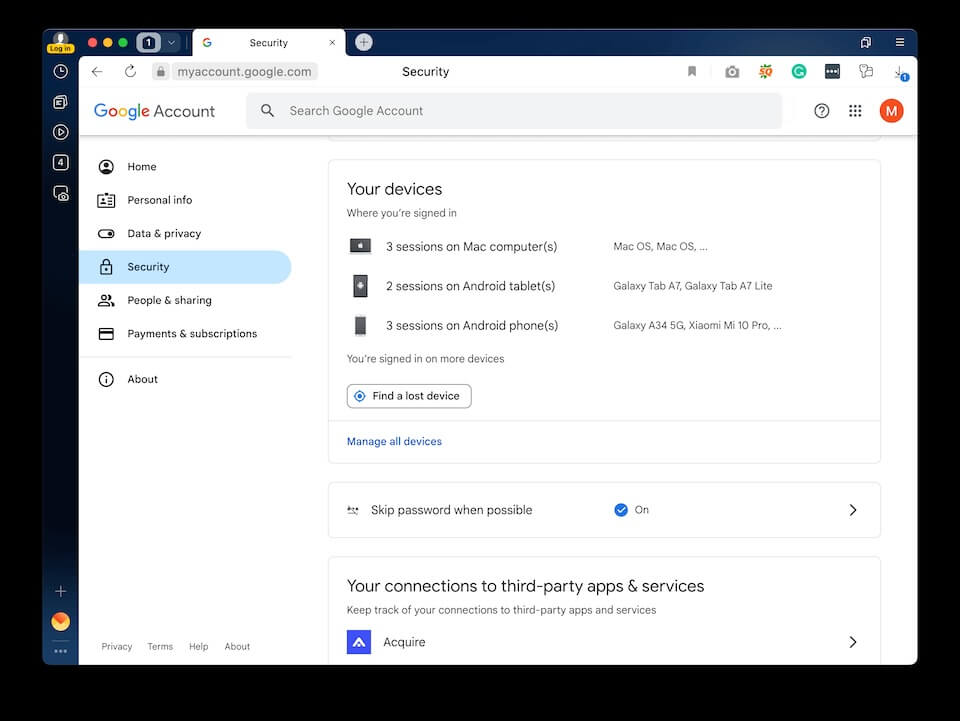
If you see something unfamiliar, tap the device’s name, then Sign out. It could be someone with unauthorized access to your account. Ignoring it can give them a chance to hack your phone.
Identify Authorized Devices on an Android Phone
To check if there are other devices linked to your Android phone, launch your smartphone’s Settings app. Depending on the brand or model, you may have to look for and tap “Linked devices” or “Connected devices.” Go through the list to ensure all items are familiar or yours.
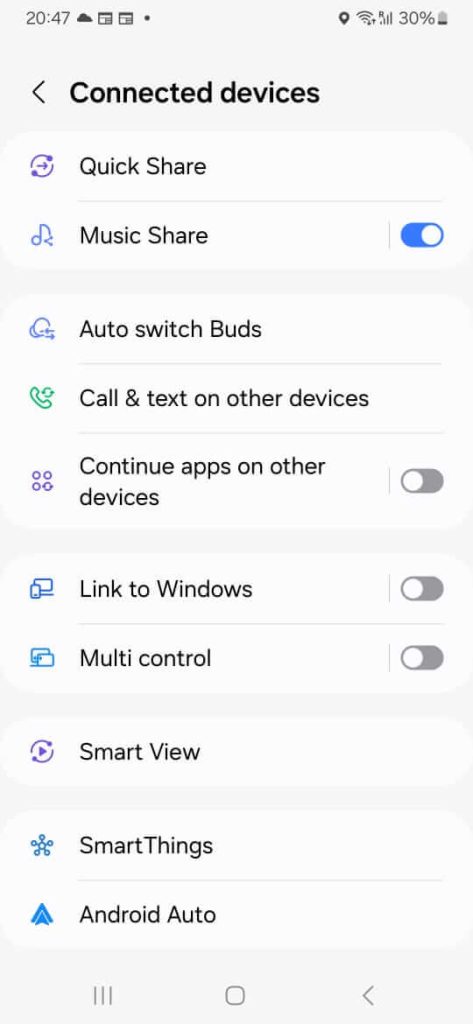
If you find one or more you don’t recognize, tap the name of each device, then select Remove, Forget, or Delete.
Check Apple ID and Linked Devices
Your Apple ID, which you may have created with your Gmail, is the account you use to access various Apple services. It’s the reason you can make all your Apple devices, such as your iPhone, iPad, and Mac, work together seamlessly. Thanks to this, you can also track your Apple Watch and AirPods.
Therefore, your Apple ID is another place to check for any device linked to your iPhone. To do this, launch the Settings app, then tap your Apple ID (your name).
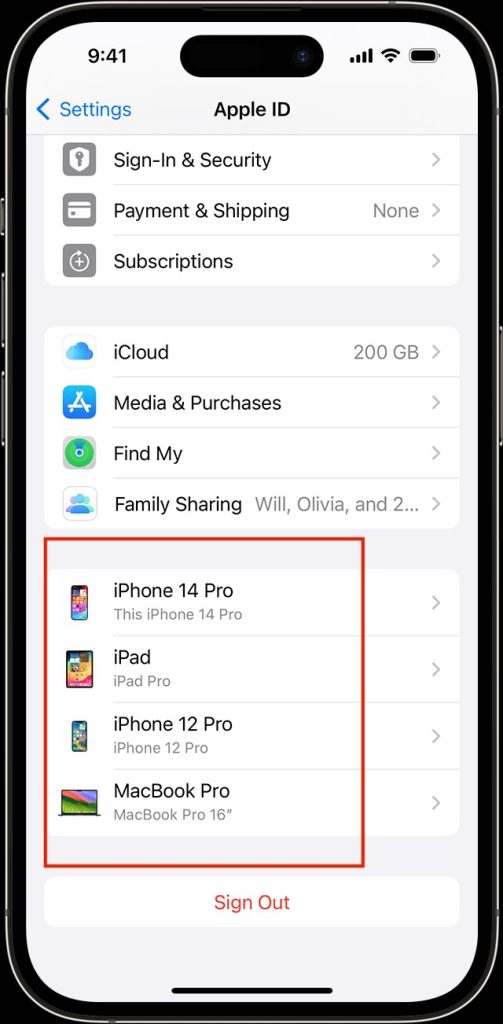
You may have to wait a few seconds as your device loads a list of devices synced to your iPhone. Check each item on the list to confirm that it’s yours. If you see a device you don’t recognize, tap its name and select Remove from Account.
You should also do the following to ensure your iPhone is secure.
Investigate iCloud for Linked Devices
iCloud is Apple’s native cloud service that lets you store and sync data across your devices. It allows you to store backups, files, and passwords online and access them on the go with your Apple ID account. It even lets you locate family and friends via Find My and find old iPhone text messages!
Since your iCloud can hold loads of data, including passwords, you must ensure it remains secure and private. Because if someone gets unauthorized access to your iPhone, they can access your iCloud account and all the sensitive data it holds.
To check your iCloud for unauthorized linkages, go to https://appleid.apple.com/. Sign in with your Apple ID credentials. Once logged in, click Sign-In and Security on the left pane under your name.
Click on the Account Security option. This should bring up a window listing your trusted phone numbers and devices. If you see any unfamiliar device there, click on its name and choose Remove from Account.
Next, return to the left pane and select the Devices option. This should show all devices associated with your Apple ID/iCloud account. Again, if there’s any device you don’t recognize, click on it and hit Remove from Account.
Explore Family Sharing
Family Sharing on iOS devices lets you, plus five other family members, share Apple services and purchases. It also allows you to set up an account for children 15 or younger and implement parental controls. It even helps you find each other’s misplaced or lost devices!
Enabling Family Sharing means syncing your phone with other devices, though. For example, you’ll share your device’s GPS signals if you use Find My to share locations with your family.
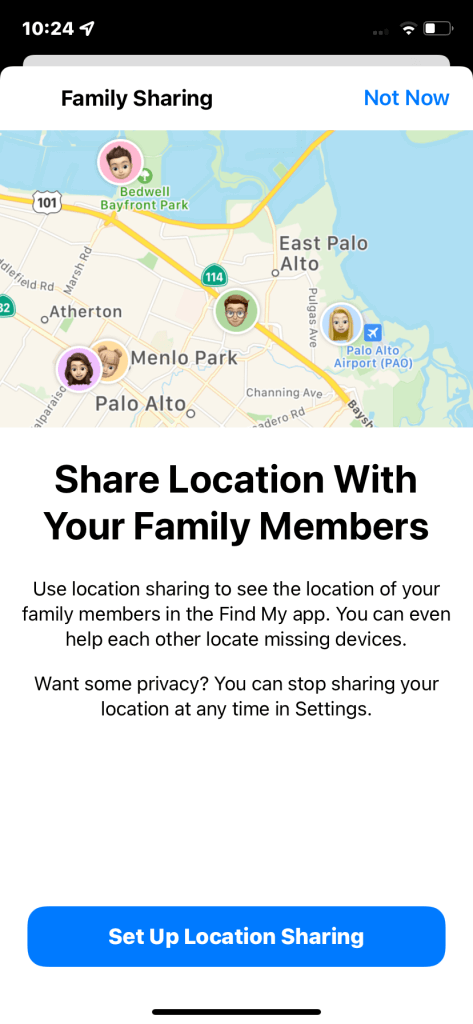
That’s wise, but you should still check your Family Sharing list to ensure only family members are on it. If someone unauthorized (such as a hacker) included themselves in it, they could gain access to your shared Apple services.
To check who’s on your Family Sharing list, open your iPhone’s Settings app, then tap Family under your Apple ID. If someone shouldn’t be in there, tap their name, then select Remove [the person’s name] from Family.
Utilizing Security Apps for Greater Peace of Mind

While the steps above can help you identify and break unauthorized device linkages, security threats don’t always show up as connected devices. They often take the form of malicious software (malware) hiding in the background.
Malware attacks have become more prevalent and cost trillions of dollars in damage each year. Those who launch such attacks often do so to rob and spy on other people or companies.
To lower your risk of becoming a malware victim, consider using security apps that scan for them. They can block and look for unauthorized device linkages, viruses, worms, and ransomware. They also have tools that can delete or quarantine such dangerous programs from your devices.
Additional Steps to Verify Device Linkages
As part of your security practices, make it a habit to check your Bluetooth Connection settings regularly. Likewise, investigate your network or Wi-Fi connection and app permissions. These can help you detect and sever unauthorized device linkages.
Checking Bluetooth Connections
As convenient as Bluetooth is, it can be vulnerable to interception by unauthorized users. For example, hackers can enforce a “Bluejacking” technique to transfer data illegally. They can also install malware on devices using this strategy.
So, check your Android or iPhone’s paired Bluetooth devices. Forget or unpair all those you don’t recognize.
You can also use your phone’s Scan for Nearby Devices feature. This can help you find devices within proximity that may link to your phone. If an unfamiliar one automatically connects to your phone, forget or unpair it ASAP.
Monitoring Wi-Fi Connections
Go through your phone’s known and saved Wi-Fi networks. Immediately forget or remove public ones.
Some advanced security apps can also scan new networks that you join. If they find anything suspicious, they’ll notify you so you can take the proper security steps. They may even prevent you from connecting to a compromised network in the first place.
Monitor App Permissions
App permissions are privileges you grant to apps downloaded onto your phone. Applications may use them to access your messages, photos, microphone, camera, or location. By law, all apps requiring such access must request your permission first.
However, dangerous programs, often created by malware developers, don’t. You don’t even have to download these applications directly. You may have downloaded an app or file compromised by these threats.
Such dangers can let hackers establish unauthorized connections with your devices.
So, always review your downloaded apps and their permissions. Immediately uninstall those you don’t recognize or need.
Reset Network Settings
Suppose your phone now has too many known networks. In this case, consider resetting your network settings to sever unauthorized links. You can then re-establish connections to trusted devices and networks after doing so.
Common Signs of Phone Linking
Phone linking, whether unauthorized or permitted, can give rise to data breaches. And according to a recent study, children are becoming prime targets. It found that data breaches exposed and potentially compromised the personal information of one in every 43 kids in the U.S.
So, be on your toes for possible unauthorized phone linking. Here are some common signs to watch out for.

Unusual Data Usage
Does your cellular data allowance seem to run out faster than before? Perhaps you’ve seen a significant increase in your phone bill charges. Another device may be piggybacking on your data, or there’s malware consuming most of it.
Increased Data Usage From Specific Apps
An unusual and sudden increase in data usage may also occur on specific apps.
To check this on an Android phone, go to Settings > Connections > Data Usage > Mobile Data Usage. For iPhone users, go to Settings > Mobile Data > Cellular.
You should see a list starting with the most often used and highest data-consuming apps. You can tap on each item to see how much data they’ve consumed in the past. Graphs showing a significant spike may indicate an unauthorized phone linkage.
Battery Drain
Any activity or process your phone has to complete uses energy. This includes maintaining the connection to linked devices. And if these devices also use your data, your phone’s battery will drain faster.
Slow Performance
Other devices linked to yours can consume your device’s resources. The same can happen if you have malware on your phone. This unnecessary resource consumption can make your phone lag and run slowly.
Unfamiliar Apps or Settings
Malicious software, including applications and viruses, can spread from one device to another. So, if an unauthorized device links to yours, it could infect your phone.
As we mentioned above, malware can install apps without device owners knowing. Thus, if you encounter one or more on your phone you don’t recognize, it could be a sign of phone linking.
Once malware infects a device, it can change settings, including those for security. It may also alter permissions, allowing apps to get even more control over your phone.
Strange Phone Behavior
Do your apps often crash or fail to load? Does your phone reboot or shut down randomly? Or maybe you encounter more and more strange pop-ups or unknown outgoing calls and texts.
Those are typical indications of unauthorized phone linking and malware infections. A hacker may also be attempting to control your device remotely.
Did you find any unfamiliar device on your Google account or phone’s “trusted” device list? That’s a sign hackers may have already accessed your device illegally.
Another is if your contacts receive unsolicited texts, chats, or emails using your number or accounts.
Suspicious Notifications
Suppose you have multi-factor authentication (MFA) enabled on your accounts. You then get an alert on your phone or email account for a One-Time PIN (OTP) or passcode. However, you didn’t do anything that warranted such a notification.
In that case, someone may have linked their device to yours and is trying to access your phone’s contents or accounts.
Practice Mobile Device Security at Home
Usually, when people ask “how to check if my phone is linked to another device,” it’s because they’ve noticed possible signs of hacking. You don’t want this to happen to you and your family, so ensure everyone knows how to keep their mobile device secure.
A comprehensive parental control and monitoring app like Family Orbit can also help make your household more cyber-secure.
So, try Family Orbit today for free! The sooner you do, the sooner you can feel more at ease about your family’s online safety and security.
- Monitor Calls & Text Messages
- View Photos and Videos
- Location Tracking & Geofence
- Monitor WhatsApp & Kik
- Detect & Alert for Inappropriate Activities
- Monitor Websites Visited
- Compatible with Android and iOS

